CCNA – Security Questions
Question 1
Explanation
We only enable PortFast feature on access ports (ports connected to end stations). But if someone does not know he can accidentally plug that port to another switch and a loop may occur when BPDUs are being transmitted and received on these ports.
With BPDU Guard, when a PortFast receives a BPDU, it will be shut down to prevent a loop -> D is correct.
Question 2
Explanation
We can verify whether port security has been configured by using the “show running-config” or “show port-security interface ” for more detail. An example of the output of “show port-security interface ” command is shown below:
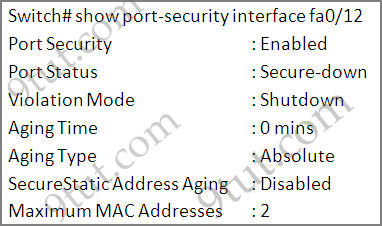
Question 3
Explanation
The full syntax of the second command is:
switchport port-security mac-address sticky [MAC]
If we don’t specify the MAC address (like in this question) then the switch will dynamically learn the attached MAC Address and place it into your running-configuration -> B is correct.
Question 4
Explanation
Please read the explanation at http://www.9tut.net/icnd2/icnd2-operations
Question 5
Explanation
Port security is only used on access port (which connects to hosts) so we need to set that port to “access” mode, then we need to specify the maximum number of hosts which are allowed to connect to this port -> C is correct.
Note: If we want to allow a fixed MAC address to connect, use the “switchport port-security mac-address ” command.
Question 6
Explanation
As we see in the output, the “Port Security” is in “Disabled” state (line 2 in the output). To enable Port security feature, we must enable it on that interface first with the command:
SwitchA(config-if)#switchport port-security
-> B is correct.
Also from the output, we learn that the switch is allowing 2 devices to connect to it (switchport port-security maximum 2) but the question requires allowing only PC_A to access the network so we need to reduce the maximum number to 1 -> D is correct.
Question 7
Explanation
Follow these guidelines when configuring port security:
+ Port security can only be configured on static access ports, trunk ports, or 802.1Q tunnel ports. -> A is not correct.
+ A secure port cannot be a dynamic access port.
+ A secure port cannot be a destination port for Switched Port Analyzer (SPAN).
+ A secure port cannot belong to a Fast EtherChannel or Gigabit EtherChannel port group. -> D is not correct
+ You cannot configure static secure or sticky secure MAC addresses on a voice VLAN. -> B is not correct.
+ When you enable port security on an interface that is also configured with a voice VLAN, you must set the maximum allowed secure addresses on the port to at least two.
+ If any type of port security is enabled on the access VLAN, dynamic port security is automatically enabled on the voice VLAN.
+ When a voice VLAN is configured on a secure port that is also configured as a sticky secure port, all addresses seen on the voice VLAN are learned as dynamic secure addresses, and all addresses seen on the access VLAN (to which the port belongs) are learned as sticky secure addresses.
+ The switch does not support port security aging of sticky secure MAC addresses.
+ The protect and restrict options cannot be simultaneously enabled on an interface.
Note: Dynamic access port or Dynamic port VLAN membership must be connected to an end station. This type of port can be configured with the “switchport access vlan dynamic” command in the interface configuration mode. Please read more about Dynamic access port here: http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3550/software/release/12-1_19_ea1/configuration/guide/3550scg/swvlan.html#wp1103064
Question 8
Explanation
One of the most widely deployed network security technologies today is IPsec over VPNs. It provides high levels of security through encryption and authentication, protecting data from unauthorized access.



Can anybody send me the ccna security(210-260) new dumps at: {email not allowed} .I will share which i am having
Can anyone send me the link of CCNP security related site.
Hello All, Could someone send me the CCNA Security 210-260 dumps to iddnk @ gmail .com
Hi, any one can tell me 338 is still valid??
@Harold Payen
can you plz share CCNA security dumps at sumreen1116 at gmail,
hi, any one can share latest dumps of 210-260 dumps dor CCNA security, I have exam end of December,
Hi,
can anybody send me the latest dumps of CCNA security(210-260).
sumreen1116 at gmail,
Hello,
can anybody send me the latest dumps of CCNA security(210-260)?
lajos.berczi at gmail.
thanks.
can anybody send me the latest dumps of CCNA security(210-260).
maha.mahmoud412 at gmail.com
Can anyone send me CCNA security dumps at m.jawaid at outlook.com
Cisco ASA Guide: https://www.cybercoastal.com/2020/04/14/cisco-firewall-technologies/
please i would like to know if there is ccna security training on 9tut
@KKF: Yes, we support Security track, please visit securitytut.com for more information about it.
Hey guys, any chance of me finding cyberops dumps. certcollection is down and i cannot find anywhere else.