Layer 2 Threats and Security Features
In this tutorial, we will learn about Layer 2 threats include DHCP Spoofing, VLAN Hopping and ARP Attack and how to use security features (DHCP snooping, VACL, Dynamic ARP Inspection) to mitigate them.
1. DHCP Spoofing:
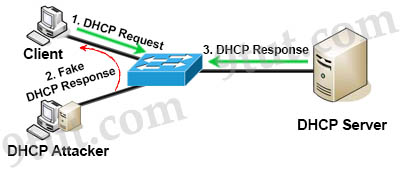
DHCP spoofing is a type of attack in that the attacker listens for DHCP Requests from clients and answers them with fake DHCP Response before the authorized DHCP Response comes to the clients. The fake DHCP Response often gives its IP address as the client default gateway -> all the traffic sent from the client will go through the attacker computer, the attacker becomes a “man-in-the-middle”.
The attacker can have some ways to make sure its fake DHCP Response arrives first. In fact, if the attacker is “closer” than the DHCP Server then he doesn’t need to do anything. Or he can DoS the DHCP Server so that it can’t send the DHCP Response.
DHCP snooping is a security feature that can prevent DHCP spoofing attacks. DHCP snooping is a Cisco Catalyst feature that determines which switch ports can respond to DHCP requests. Ports are identified as trusted and untrusted.
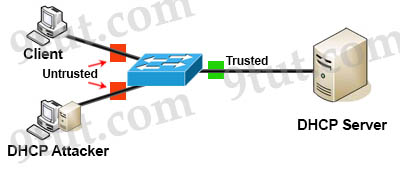
Only ports that connect to an authorized DHCP server are trusted, and allowed to send all types of DHCP messages. All other ports on the switch are untrusted and can send only DHCP requests. If a DHCP response is seen on an untrusted port, the port is shut down.
2. VLAN Hopping: By altering the VLAN ID on packets encapsulated for trunking, an attacking device can send or receive packets on various VLANs, bypassing Layer 3 security measures. VLAN hopping can be accomplished by switch spoofing or double tagging.
a. Switch spoofing:
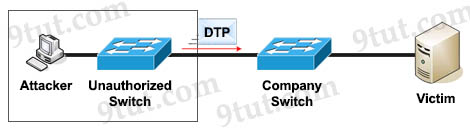
The attacker can connect an unauthorized Cisco switch to a Company switch port. The unauthorized switch can send DTP frames and form a trunk with the Company Switch. If the attacker can establish a trunk link to the Company switch, it receives traffic to all VLANs through the trunk because all VLANs are allowed on a trunk by default.
(Instead of using a Cisco Switch, the attacker can use a software to create and send DTP frames).
To mitigate this type of attack, we can disable DTP.
b. Double-Tagging attack:
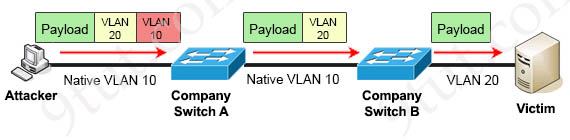
In this attack, the attacking computer generates frames with two 802.1Q tags. The first tag matches the native VLAN of the trunk port (VLAN 10 in this case), and the second matches the VLAN of a host it wants to attack (VLAN 20).
When the packet from the attacker reaches Switch A, Switch A only sees the first VLAN 10 and it matches with its native VLAN 10 so this VLAN tag is removed. Switch A forwards the frame out all links with the same native VLAN 10. Switch B receives the frame with an tag of VLAN 20 so it removes this tag and forwards out to the Victim computer.
Note: This attack only works if the trunk (between two switches) has the same native VLAN as the attacker. In other words, this attack is only successful if the attacker belongs to the native VLAN of the trunk link. Another important point is, this attack is strictly one way as it is impossible to encapsulate the return packet.
To mitigate this type of attack, we can use VLAN access control lists (VACLs, which applies to all traffic within a VLAN. We can use VACL to drop attacker traffic to specific victims/servers); or implement Private VLANs; or keep the native VLAN of all trunk ports different from user VLANs.
3. ARP attack (like ARP poisoning/spoofing) is a type of attack in which a malicious actor sends falsified ARP messages over a local area network as ARP allows a gratuitous reply from a host even if an ARP request was not received. This results in the linking of an attacker’s MAC address with the IP address of a legitimate computer or server on the network. This is an attack based on ARP which is at Layer 2.
Dynamic ARP inspection (DAI) is a security feature that validates ARP packets in a network which can be used to mitigate this type of attack.
4. MAC flooding attack
In this attack, the hacker first connects to a switch port and floods it with frames (packets), each containing different source MAC addresses. As we know, the switch must record these source MAC addresses to CAM table for later use. The problem is the size of the CAM table is limited. Once there is no space to store the fake MAC addresses, the switch enter a state called failopen mode. In this state, all incoming packets are broadcast out on all ports (like a hub), instead of just down the correct port as per normal operation.
The hacker finally uses a packet sniffer to capture sensitive data from other computers, which would not be accessible were the switch operating normally.
In order to prevent this type of attack, the administrator can configure port-security feature, which limits the number of MAC addresses on each switch port. Or configure 802.1x authentication, which checks a user’s credentials to see if the users are an active member of the organization and grants users varying levels of access to the network.



so what can you do against VLAN Hopping ?
@smounche: To mitigate this type of attack, you can use VLAN access control lists (VACLs, which applies to all traffic within a VLAN. We can use VACL to drop attacker traffic to specific victims/servers) or implement Private VLANs.
hello from the other side
so what can you do against VLAN Hopping to p ?
Who wants to know how to INSTALL L2 SWITCH in GNS3?
Greetings everyone
Very good Tutorials
Hey ,
I found Security Vulnerability in your web application. For security purpose can we report vulnerability here,then will i get bounty reward in PayPal or Bitcoin for Security bug ?
Thanks
Independent security researcher
any cisco collaboration exam questions?
I didnt understand ARP attack, can someone help with an example please?
Dear Folks, in premium account how many ccna questions we need to prepare for the exam. Thanks
Does anyone have VCE Player cracked version?
https://certbulls.org/index.php?/topic/7-basic-python-scripts-for-network-engineer/&tab=comments#comment-9
cna 200-301 official cert guide?
How can I prevent doubletagging attack
Where to download latest VCE for CCNA?
Hello everyone i will ask the community here how can i download the questions and answer for last CCNA from site i am premium member but i need pdf file thanks for all help have a good night.
In this attack, the hacker first connects to a switch port and floods it with packets, each containing different source MAC addresses…
Is this worded corrected? How does a switch deal with packets? Should this be worded as frames?
@Anonymous: In fact the meaning between “packets” and “frames” here are the same. They are just called differently in the OSI model. But we also updated it. Thank you for your detection!