Wireless Questions
Note: If you are not sure about Wireless, please read our Wireless tutorial.
|
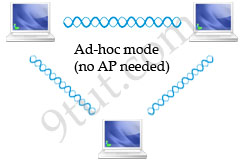
Quick Wireless Summary WLAN Modes: WLAN has two basic modes of operation: * Ad-hoc mode: In this mode devices send data directly to each other without an AP.
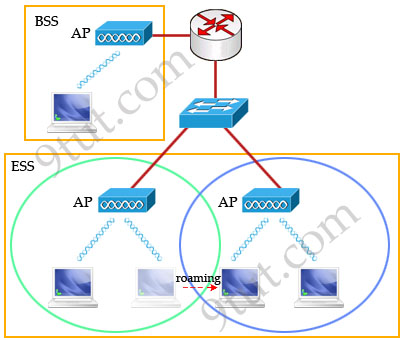
* Infrastructure mode: Connect to a wired LAN, supports two modes (service sets): + Basic Service Set (BSS): uses only a single AP to create a WLAN
Roaming: The ability to use a wireless device and be able to move from one access point’s range to another without losing the connection. Cisco Access Points (APs) can operate in one of two modes: autonomous or lightweight An LAP operates in one of six different modes:
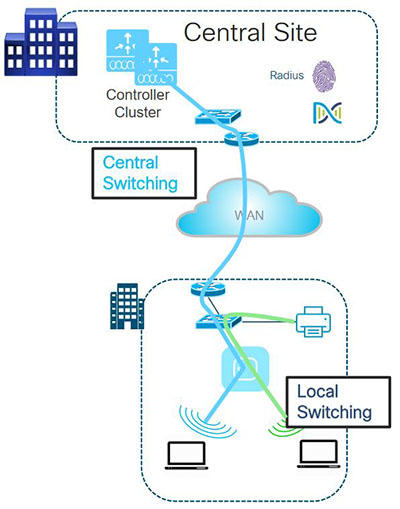
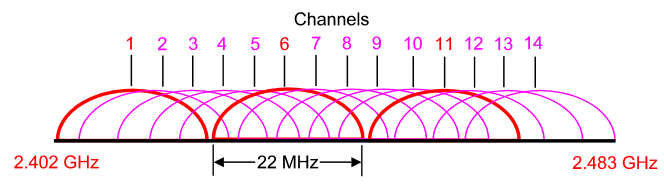
FlexConnect addresses the wireless connectivity needs in branch locations by permitting wireless user traffic to terminate locally rather than tunneled across the WAN to a central WLC. – Control and Provisioning for Wireless Access Point (CAPWAP) is an IETF standard protocol which enables a WLC to manage multiple APs. CAPWAP is similar to LWAPP except the following differences: + CAPWAP uses Datagram Transport Layer Security (DTLS) for authentication and encryption to protect traffic between APs and controllers. LWAPP uses AES. Signal to Noise Ratio (SNR) is defined as the ratio of the transmitted power from the AP to the ambient (noise floor) energy present. To calculate the SNR value, we add the Signal Value to the Noise Value to get the SNR ratio. A positive value of the SNR ratio is always better. The 2.4 GHz band is subdivided into multiple channels each allotted 22 MHz bandwidth and separated from the next channel by 5 MHz.
Types of external antennas: WPA2 and WPA3 WPA2 is classified into two versions to encrypt Wi-Fi networks: Similar to WPA2, WPA3 includes: WPA3 uses AES encryption and SAE for authentication methods. WPA3 provides improvements to the general Wi-Fi encryption, thanks to Simultaneous Authentication of Equals (SAE) replacing the Pre-Shared Key (PSK) authentication method used in prior WPA versions. With SAE, the user experience is the same (choose a passphrase to connect), but SAE automatically adds a step to the handshake, which makes brute force attacks ineffective. SAE enables individuals or home users to set Wi-Fi passwords that are easier to remember and provide the same security protection even if the passwords are not complex enough. WPA3 requires the use of Protected Management Frames. These frames help protect against forging and eavesdropping. WPA3 networks include perfect forward secrecy. With this protection, even if an adversary successfully guesses the correct network password, they cannot observe a user’s earlier interactions on the network, determine the session keys for that interaction, or decrypt wireless traffic from other users on the network Wireless Standards
WLC terms A dynamic interface is an interface that maps a WLAN to a wired VLAN or subnet. Dynamic interfaces are used to control and secure the traffic on the WLAN just like we use VLANs and subnets on the LAN for that purpose. Interface groups are logical groups of interfaces. An interface can be part of multiple interface groups. When many APs support the same WLAN, all users of that WLAN, on all APs connected to the same controller, are sent to the same dynamic interface. By default there is a AP Group called “default-group” created on your WLC and all the WLANs where WLAN ID is between 1-16 map to this group. |
Question 1
Explanation
Many routers provide WPA2-PSK (TKIP), WPA2-PSK (AES), and WPA2-PSK (TKIP/AES) as options. TKIP is actually an older encryption protocol introduced with WPA to replace the very-insecure WEP encryption at the time. TKIP is actually quite similar to WEP encryption. TKIP is no longer considered secure, and is now deprecated. In other words, you shouldn’t be using it.
AES is a more secure encryption protocol introduced with WPA2 and it is currently the strongest encryption type for WPA2-PSK.
Question 2
Explanation
In previous releases, whenever a FlexConnect access point disassociates from a controller, it moves to the standalone mode. The clients that are centrally switched are disassociated. However, the FlexConnect access point continues to serve locally switched clients. When the FlexConnect access point rejoins the controller (or a standby controller), all clients are disconnected and are authenticated again. This functionality has been enhanced and the connection between the clients and the FlexConnect access points are maintained intact and the clients experience seamless connectivity. When both the access point and the controller have the same configuration, the connection between the clients and APs is maintained.
Question 3
Explanation
Cisco Unified Wireless Network solution WLANs support four levels of QoS: Platinum/Voice, Gold/Video, Silver/Best Effort (default), and Bronze/Background.
Question 4
Question 5
Explanation
Link aggregation (LAG) is a partial implementation of the 802.3ad port aggregation standard. It bundles all of the controller’s distribution system ports into a single 802.3ad port channel.
Restriction for Link aggregation:
+ LAG requires the EtherChannel to be configured for ‘mode on’ on both the controller and the Catalyst switch -> Answer B is not correct.
+ If the recommended load-balancing method cannot be configured on the Catalyst switch, then configure the LAG connection as a single member link or disable LAG on the controller -> Answer A is not correct while answer D is correct.
Question 6
Explanation
A Lightweight Access Point (LAP) is an AP that is designed to be connected to a wireless LAN (WLAN) controller (WLC). APs are “lightweight,” which means that they cannot act independently of a wireless LAN controller (WLC). The WLC manages the AP configurations and firmware. The APs are “zero touch” deployed, and individual configuration of APs is not necessary.
Reference: https://www.cisco.com/c/en/us/support/docs/wireless/aironet-1200-series/70278-lap-faq.html
Question 7
Explanation
WPA2
Pros:
+ Addresses many security flaws of its predecessors
+ Uses the strongest encryption method: AES
+ Required by the Wi-Fi Alliance for use on all Wi-Fi certified products
+ 256-bit key for encryption
Reference: https://www.avast.com/c-wep-vs-wpa-or-wpa2
Question 8
Question 9
Explanation
Whenever you want to control which devices can talk to the main CPU, a CPU ACL is used.
Note: CPU ACLs only filter traffic towards the CPU, and not any traffic exiting or generated by the CPU.
Question 10
Explanation
There are three main types of 802.11 frames: the Data Frame, the Management Frame and the Control Frame. Association Response belongs to Management Frame. Association response is sent in response to an association request.
Question 11
Explanation
When configuring a WLAN with WPA2 Preshared Key (PSK), we can choose the encryption key format as either ASCII or HEX.
Question 12
Question 13
Explanation
The 802.11 standard defines 23 20MHz wide channels in the 5 GHz spectrum. Each channel is spaced 20MHz apart and separated into three Unlicensed National Information Infrastructure (UNII) bands.
Reference: https://documentation.meraki.com/MR/WiFi_Basics_and_Best_Practices/Channel_Planning_Best_Practices



Hi Guys,
I can’t see the questions!
@Farshad get the premium membership to see them.
@9tut, why on Q13 E is marked as a right answer?
Two neighbor (adjacent) APs on the same channel would interfere.
@Alex: Thanks for your detection, we have just fixed Q.13.
in the quiz, answer 13 is not yet corrected.
q7 answer is aes- 128.
“WPA 2 is the next generation of Wi-Fi security. ….. recommended Advanced Encryption Standard (AES) encryption algorithm with the use of Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP). AES Counter Mode is a block cipher that encrypts 128-bit blocks of data at a time with a 128-bit encryption key. The CCMP algorithm produces a message integrity code (MIC) that provides data origin authentication and data integrity for the wireless frame.”
source: https://www.cisco.com/c/en/us/support/docs/wireless-mobility/wireless-lan-wlan/67134-wpa2-config.html
@9tut could you confirm about q7 which said by @Erbucharest. I believe he is correct
so i test next week….I’ve studied the books and watched the videos and am using this as more of a “I don’t want to have to spend another 300 bucks if I fail” has anyone taken it recently? Are these pretty close to the questions on the test?
“WPA 2 is the next generation of Wi-Fi security. WPA 2 is the Wi-Fi Alliance interoperable implementation of the ratified IEEE 802.11i standard. WPA 2 implements the National Institute of Standards and Technology (NIST)-recommended Advanced Encryption Standard (AES) encryption algorithm with the use of Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP). AES Counter Mode is a block cipher that encrypts 128-bit blocks of data at a time with a 128-bit encryption key”
source: https://www.cisco.com/c/en/us/support/docs/wireless-mobility/wireless-lan-wlan/67134-wpa2-config.html
C is correct