Drag Drop Questions 3
Question 1
Explanation
An AAAA record maps a domain name to the IP address (Version 6) of the computer hosting the domain. An AAAA record is used to find the IP address of a computer connected to the internet from a name. The AAAA record is conceptually similar to the A record, but it allows you to specify the IPv6 address of the server, rather than the IPv4. An example of AAAA is the ‘www’ of 9tut.com is pointed to 2001:0db8:aaaa:bbbb:cccc:dddd:eeee:ffff.
NS (name server) looks like a website URL, but instead of linking to a website, they link to the domain names authoritative nameservers. An example of a NS is ‘ns1.9tut.com’.
The Canonical Name record (CNAME) tells anyone visiting that subdomain to use the same DNS records as another domain / subdomain. If you are already using an A or AAAA record for a subdomain you wouldn’t use a CNAME. CNAME records must always point to another domain / subdomain, never directly to an IP address. For example, we can configure the CNAME of www.9tut.com points to 9tut.com so that they use the same IP address.
As opposed to forward DNS resolution (A and AAAA DNS records), the Reverse-lookup Pointer (PTR) record is used to look up domain names based on an IP address.
An SOA record or start of authority record specifies the DNS server providing authoritative information about an Internet domain, the email of the domain administrator, the domain serial number, and several timers relating to refreshing the zone.
An example of a SOA record is shown below.
; name TTL class rr Nameserver email-address mydomain.com. 14400 IN SOA ns.mynameserver.com. root.ns.mynameserver.com. ( 2004123001 ; Serial number 86000 ; Refresh rate in seconds 7200 ; Update Retry in seconds 3600000 ; Expiry in seconds 600 ; minimum in seconds )
name – mydomain.com is the main name in this zone.
TTL – 14400 – TTL defines the duration in seconds that the record may be cached by client side programs. If it is set as 0, it indicates that the record should not be cached. The range is defined to be between 0 to 2147483647 (close to 68 years !) .
Class – IN – The class shows the type of record. IN equates to Internet. Other options are all historic. So as long as your DNS is on the Internet or Intranet, you must use IN.
Nameserver – ns.nameserver.com. – The nameserver is the server which holds the zone files. It can be either an external server in which case, the entire domain name must be specified followed by a dot. In case it is defined in this zone file, then it can be written as “ns” .
Email address – root.ns.nameserver.com. – This is the email of the domain name administrator. Now, this is really confusing, because people expect an @ to be in an email address. However in this case, email is sent to root@ns.nameserver.com, but written as root.ns.nameserver.com . And yes, remember to put the dot behind the domain name.
Serial number – 2004123001 – This is a sort of a revision numbering system to show the changes made to the DNS Zone. This number has to increment , whenever any change is made to the Zone file. The standard convention is to use the date of update YYYYMMDDnn, where nn is a revision number in case more than one updates are done in a day. So if the first update done today would be 2005301200 and second update would be 2005301201.
Refresh – 86000 – This is time(in seconds) when the slave DNS server will refresh from the master. This value represents how often a secondary will poll the primary server to see if the serial number for the zone has increased (so it knows to request a new copy of the data for the zone). It can be written as “23h88M” indicating 23 hours and 88 minutes. If you have a regular Internet server, you can keep it between 6 to 24 hours.
Retry – 7200 – Now assume that a slave tried to contact the master server and failed to contact it because it was down. The Retry value (time in seconds) will tell it when to get back. This value is not very important and can be a fraction of the refresh value.
Expiry – 3600000 – This is the time (in seconds) that a slave server will keep a cached zone file as valid, if it can’t contact the primary server. If this value were set to say 2 weeks ( in seconds), what it means is that a slave would still be able to give out domain information from its cached zone file for 2 weeks, without anyone knowing the difference. The recommended value is between 2 to 4 weeks.
Minimum – 600 – This is the default time(in seconds) that the slave servers should cache the Zone file. This is the most important time field in the SOA Record. If your DNS information keeps changing, keep it down to a day or less. Otherwise if your DNS record doesn’t change regularly, step it up between 1 to 5 days. The benefit of keeping this value high, is that your website speeds increase drastically as a result of reduced lookups. Caching servers around the globe would cache your records and this improves site performance.
Question 2
Explanation
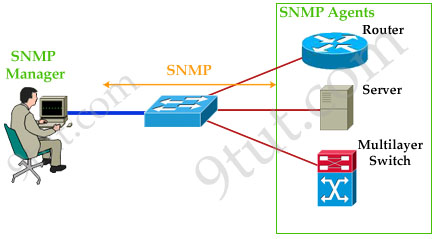
SNMP consists of 3 items:
+ SNMP Manager (sometimes called Network Management System – NMS): a software runs on the device of the network administrator (in most case, a computer) to monitor the network.
+ SNMP Agent: a software runs on network devices that we want to monitor (router, switch, server…)
+ Management Information Base (MIB): is the collection of managed objects. This components makes sure that the data exchange between the manager and the agent remains structured. In other words, MIB contains a set of questions that the SNMP Manager can ask the Agent (and the Agent can understand them). MIB is commonly shared between the Agent and Manager.
Question 3
Explanation
Note: The “Wireless LAN adapter Local Area Connection *6” is not physical LAN connection. Those are just Virtual drivers (simulated network adapters) that are installed by Windows for something like Hyper-V. Real, physical NICs get numbered “Ethernet ###” (or “Wireless ###”, etc.)
Question 4
Explanation
This question says “permit only two random MAC addresses at a time” so we cannot use the “switchport port-security mac-address sticky” command as the switch will only learn and save the first two MAC addresses forever. Although the command “switchport port-security violation shutdown” is unnecessary because it is the default state of port-security but it is not wrong to reuse it.
Note:
The full syntax of the second command is:
switchport port-security mac-address sticky [MAC]
If we don’t specify the MAC address (like in this question) then the switch will dynamically learn the attached MAC Address and place it into your running-configuration.
Question 5
Explanation
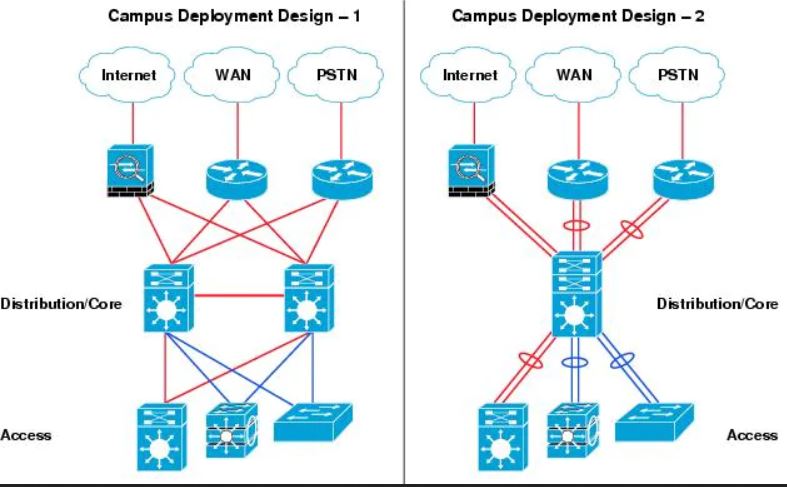
The three-tier hierarchical design maximizes performance, network availability, and the ability to scale the network design.
However, many small enterprise networks do not grow significantly larger over time. Therefore, a two-tier hierarchical design where the core and distribution layers are collapsed into one layer is often more practical. A “collapsed core” is when the distribution layer and core layer functions are implemented by a single device. The primary motivation for the collapsed core design is reducing network cost, while maintaining most of the benefits of the three-tier hierarchical model.
Reference: https://www.ciscopress.com/articles/article.asp?p=2202410&seqNum=4
A collapsed core network is shown below. The collapsed core network may be deployed with redundant core/distribution router, or consolidated core/distribution router.
Question 6
Explanation
First-in, first-out (FIFO): FIFO entails no concept of priority or classes of traffic. With FIFO, transmission of packets out the interface occurs in the order the packets arrive, which means no QoS
Priority Queuing (PQ): This type of queuing places traffic into one of four queues. Each queue has a different level of priority, and higher-priority queues must be emptied before packets are emptied from lower-priority queues. This behavior can “starve out” lower- priority traffic.
Custom Queuing (CQ): provide specific traffic guaranteed bandwidth at a potential congestion point, assuring the traffic a fixed portion of available bandwidth and leaving the remaining bandwidth to other traffic.
Weighted fair queueing (WFQ): offers dynamic, fair queuing that divides bandwidth across queues of traffic based on weights. In standard WFQ, packets are classified into flows according to one of four criteria: the source Internet Protocol address (IP address), the destination IP address, the source Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) port, or the destination TCP or UDP port.
Class-based weighted fair queueing (CBWFQ) extends the standard WFQ functionality to provide support for user-defined traffic classes. For CBWFQ, you define traffic classes based on match criteria including protocols, access control lists (ACLs), and input interfaces. Packets satisfying the match criteria for a class constitute the traffic for that class. A queue is reserved for each class, and traffic belonging to a class is directed to the queue for that class.
Once a class has been defined according to its match criteria, you can assign it characteristics. To characterize a class, you assign it bandwidth, weight, and maximum packet limit. The bandwidth assigned to a class is the guaranteed bandwidth delivered to the class during congestion.
Question 7
Question 8



Question 6 – Think PQ and WFQ should be switched?
Answer:
PQ = places packets into one of four priority-based queues
WFQ = provides minimum guaranteed bandwidth to one or more flows
@j: Yes, thanks for your detection, we have just updated Q.6!
can someone check the questions are missing?
Question 4 It said to permit only two random MAC addresses at a time. In the sticky it will only learn 2 Mac address the first 2 so it will not permit only two RANDOM MAC address at a time. Instead the question doesnt say anything for what to do in a violation case. So i believe correct answers
1: switchport mode access
2: switchport port-security
3: switchport port-security maximum 2
4: switchport port-security violation shutdown (which is the default option of a port-security but it isnt wrong to do it)
Furthermore with the setting of maximum 2 we only permit 2 MAC address at a time.Default is dynamically learn
@9tut could you aggree or disaggree ?
@Anonym: Thanks for your information, we updated Q4!
Hey! I have planned to make CCNA in the next 3-6 months, is it somebody that can give me tips and tricks please and the latest exams questions. Would appreciete it! Send to my email yasinosmandun12@gmail.c o m