We have many tutorials and practice labs on our site to help you understand the concepts of the CCNA exam. We have summarized them here in one place and categorized them into specific topics to make your learning easier.
================== CCNA Tutorials ==================
================= CCNA Practice Labs =================
Practice labs help individuals and professionals gain practical experience with networking technologies by configuring routers & switches on the emulators
================ CCNA Lab Challenges ================
Lab Challenges require you to configure or troubleshooting preconfigured labs
Spine-leaf architecture is a modern network topology widely used in data centers and cloud environments. It’s designed to offer improved scalability, high availability, and consistent low-latency communication. Unlike traditional three-tiered hierarchical networks (core, distribution, access layers), the spine-leaf architecture consists of only two layers of switches: spine and leaf switches.
|
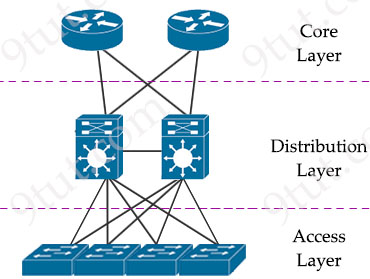
Traditional three-tier architecture
|
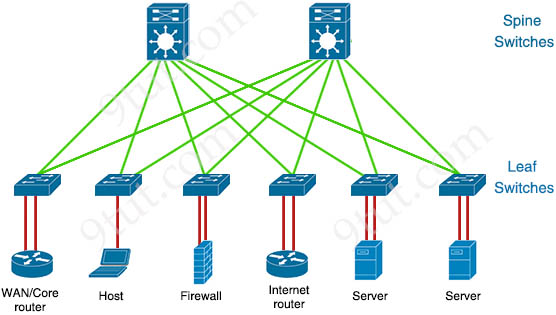 Spine-Leaf Architecture Spine-Leaf Architecture |
The spine layer consists of switches that perform routing and work as the core of the network. The leaf layer involves access switches that connect to servers, storage devices, and other end-users. This structure helps data center networks reduce hop count, reduce network latency and prevent bottlenecks, which are main issues of three-tier architecture.
READ MORE…
Artificial intelligence (AI) is full of concepts that seem familiar at first glance, but often reveal much more complexity upon closer examination. One such example is the distinction between Generative AI and Predictive AI. These terms are often confused, but understanding the difference is crucial. Let’s explore them in more detail.

READ MORE…
An API (Application Programming Interface) allows different software applications to communicate with each other. It defines the methods and data formats that applications can use to request and exchange data.
REST (REpresentational State Transfer) is an architectural style for designing networked applications. It relies on a stateless, client-server, cacheable communications protocol – the HTTP. RESTful applications use HTTP requests to perform CRUD (Create, Read, Update, Delete) operations on resources and return data in various formats, often JSON or XML.
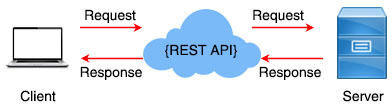
An API that follows the REST standard is called a RESTful API or REST API. A REST implementation should be stateless. It means the two parties don’t need to store any information about each other, and every request and response (cycle) is independent from all others. It uses standard HTTP methods and can return data in various formats, often JSON or XML. READ MORE…
The Network Time Protocol (NTP) is a crucial service not only for Cisco devices but for most network devices. Any device needs to be accurately synchronized with a reliable time source such as an NTP server.
For networking devices, precise timekeeping is very important because many services depend on it. A common and frequently used example is logging and SNMP.
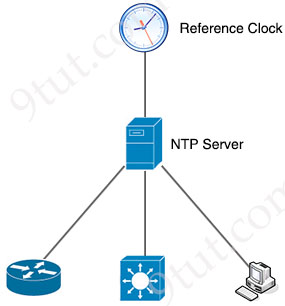
READ MORE…
DHCP Snooping is a Layer 2 security feature that can be configured on a switch to listen DHCP traffic and block DHCP OFFER and DHCP ACK packets (which can only be sent from a DHCP server) on untrusted ports.
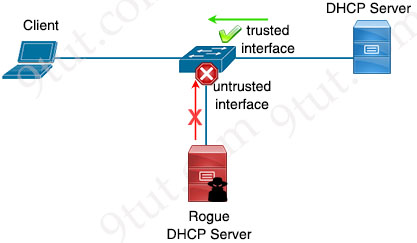
DHCP Snooping is very easy to configure. We only need to:
1. Turn this feature on the switch
2. Configure trusted interface(s). Other interfaces are untrusted by default.
Trusted interface is the interface that is connected to our DHCP server so that all DHCP messages are allowed.
DHCP Snooping feature also creates a table of IP – MAC address mapping which lists client MAC addresses, DHCP-assigned IP addresses…
READ MORE…
Most traditional devices use a distributed architecture, in which each control plane is resided in a networking device. Each device will make its own decision. Therefore they need to communicate with each other via messages to work correctly.
In contrast to distributed architecture, centralized (or controller-based) architectures centralizes the control of networking devices into one device, called SDN controller. This is also the main idea when creating SDN. In other words, SDN creates a king to control the whole networking kingdom!

READ MORE…
We all know when a packet reaches a router interface, the router will send the packet to the destination. But how can a router determines which route is the best to use to send the packet? In this tutorial we will learn more about how a router makes the forwarding decision.
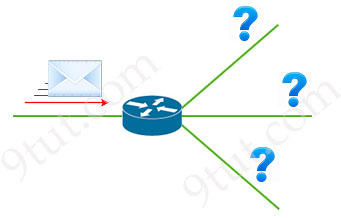
To make the routing decision, the router must first build a table which contains all the best routes. When the packets arrive, the router just needs to check this table to choose the best match. This is called the routing table.
READ MORE…
One of the most popular way to access a Cisco router remotely is using Telnet but it is an unsecured method as the data is sent unencrypted. If a bad person grabs data from a Telnet session, he can see details like a user’s username and password, giving them access to your router.
SSH (Secure Shell) is a secure method for remote access as it includes authentication and encryption. To do this, it uses a RSA public/private keypair. In this tutorial we are going to learn how to configure SSH for R1 to accept remote SSH access with the topology below.

READ MORE…
In the digital world, where we use computers and the internet for many things, keeping our information safe is one of the most important tasks. This tutorial will explore some of the popular and important security concepts, making it easier for us to understand and use them to keep our online world secure and private.
Let’s take an example of a common house, which is typically built using bricks, stones, or concrete blocks. They are very strong materials which are considered to be secure from theft. But a house cannot be used easily without doors and windows so that the owners can enter and exit using keys. But it means anyone else can gain access as well with some hand tools. The doors and windows (and chimney) are considered vulnerabilities.
In cybersecurity, a vulnerability refers to a weakness or flaw in a system’s design, implementation, or operation that could be exploited by attackers to compromise the system’s security.

READ MORE…
Quality of Service (QoS) is a tool that allows our network to prioritize certain types of traffic. QoS defines the actions that a device can apply to a message between the time it enters the device until it exits the device. These actions are called per-hop behaviors (PHBs). With PHBs, we can discard, delay, or even change the header field of each packet. The goal of a PHB is to provide a specified amount of network resources to a class of traffic on a contiguous network.
PHB uses a set of codepoints to mark packets with different levels of priority. These codepoints are embedded in the Differentiated Services Code Point (DSCP) field of the Type Of Service (ToS) field of the IP header.
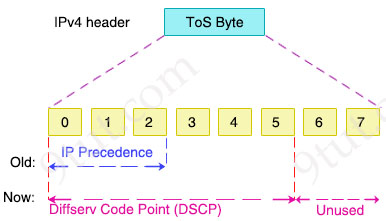
READ MORE…
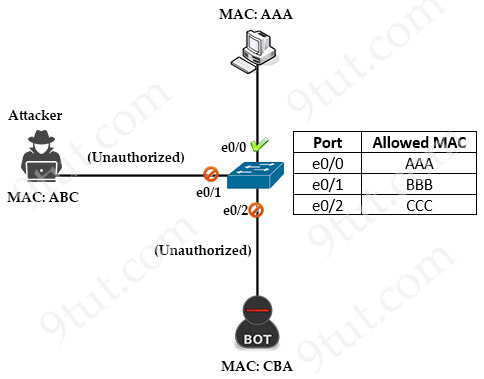
By default, all interfaces on a Cisco switch are in an enabled state, meaning that anyone can potentially connect to your network through a wall socket, posing a security risk. Port Security is a feature that enhances the security of Cisco switches by controlling access to Ethernet ports based on the MAC addresses of connected devices.
Port Security allows network administrators to associate only specific MAC addresses or set a maximum number of MAC addresses with each switch port. This association restricts access to the interface, ensuring that only authorized devices with recognized MAC addresses can use it. If an unauthorized device attempts to connect, you can configure the switch to take predefined actions, such as discarding the incoming traffic, sending a warning message or shutting down the port to mitigate the security threat.
In the figure below, only host with MAC address of AAA (just for example. In fact the MAC address must be 48 bits) was configured to connect to the switch port while other MAC addresses are blocked:
READ MORE…
Besides Ansible and Chef, Puppet is another automation tool in CCNA certification so in this tutorial we will learn about it.
Puppet is built on server-client architecture which comprises a master (centralized server) and some/many nodes (clients). In each node, a Puppet Agent is installed to communicate with the Puppet Master. Puppet Master is the place where all Puppet codes are written and stored. These codes dictate the instructions for performing various tasks for the client. If the Clients need something, they simply request them.
Puppet is based on a Pull deployment model, where the nodes check in regularly after every 1800 seconds with the Master to see if anything needs to be updated in the agent. If anything needs to be updated the agent pulls the necessary Puppet codes from the Master and performs required actions.
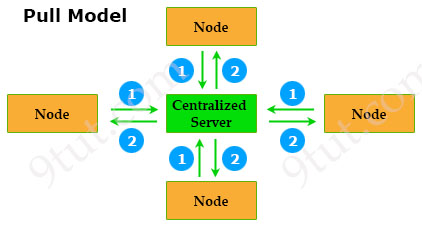
READ MORE…
Chef is an automation platform that configures and manages your network infrastructure. Chef transforms infrastructure into code. “Infrastructure into code” here means “deploy your code/application/configuration and policy” on many machines or instances automatically via your code.
As shown in the diagram below, there are three major Chef components:
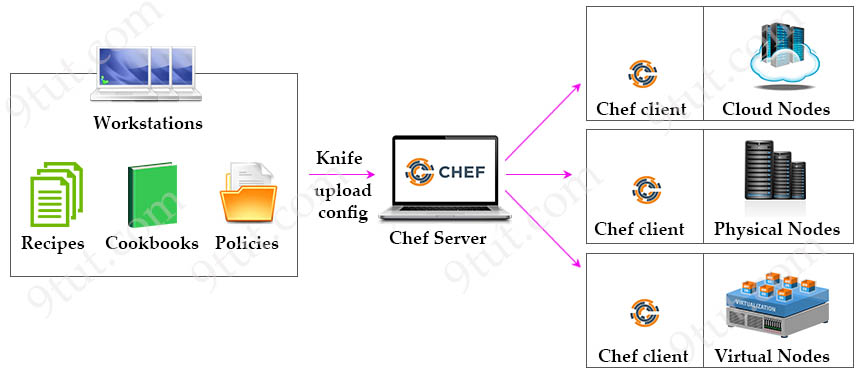
READ MORE…
There are several automation tools available to make configuration management easier: Ansible, Chef, Puppet… The goal of these tools is to reduce the complexity and time to configure and maintain networks (especially big ones with hundreds of devices). In this tutorial we will learn some basic knowledge of Ansible in the scope of CCNA level.
Ansible uses an agentless architecture to manage network devices. Agentless means that the managed device does not need any code (agent) to be installed on it. Therefore Ansible uses SSH (NETCONF over SSH in particular) to “push” changes and extract information to managed devices.
Once Ansible is installed, it creates several text files:
+ Playbooks: These files provide actions and logic about what Ansible should do. Ansible playbooks are files that contain tasks to configure hosts. Ansible playbooks are written in YAML format. Inside Playbooks, we have:
++ Modules (also referred to as “task plugins” or “library plugins”) are discrete units of code that can be used from the command line or in a playbook task. Ansible executes each module, usually on the remote managed node, and collects return values.
++ Tasks: Tasks are Ansible’s smallest unit of work. They are a series of actions on the target hosts, using modules to provide functionalities.
A task defines an action that needs to be performed, while a module executes the action on a managed host.
+ Inventory: a file contains a list of the hosts (usually their IP addresses, ports) which you want to configure or manage. Hosts in an inventory can be divided into smaller groups for easier management and configuration. Each group can run different tasks. An example of a task is to ping all hosts in group [routers].
+ Templates: Using Jinja2 language, the templates represent a device’s configuration but with variables.
+ Variables: Using YAML, a file can list variables that Ansible will substitute into templates.
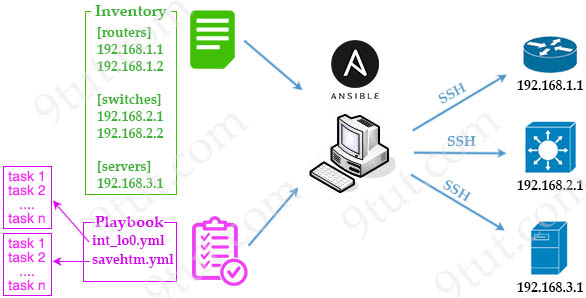
READ MORE…
JavaScript Object Notation (JSON) is a human readable and very popular format used by web services, programming languages (including Python) and APIs to read/write data. JSON is also a subject of the CCNA 200-301 so in this article we will learn some basic knowledge of JSON and how to use Python to process JSON.
JSON syntax structure:
+ uses curly braces {} to hold objects and square brackets [] to hold arrays
+ JSON data is written as key/value pairs
+ A key/value pair consists of a key (must be a string in double quotation marks ""), followed by a colon :, followed by a value. For example: “name”:”John”
+ Each key must be unique
+ Values must be of type string, number, object, array, boolean or null
+ Multiple key/value within an object are separated by commas ,
READ MORE…
In this tutorial, we will learn about Layer 2 threats include DHCP Spoofing, VLAN Hopping and ARP Attack and how to use security features (DHCP snooping, VACL, Dynamic ARP Inspection) to mitigate them.
1. DHCP Spoofing:
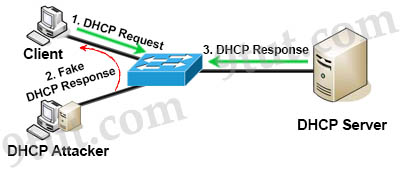
DHCP spoofing is a type of attack in that the attacker listens for DHCP Requests from clients and answers them with fake DHCP Response before the authorized DHCP Response comes to the clients. The fake DHCP Response often gives its IP address as the client default gateway -> all the traffic sent from the client will go through the attacker computer, the attacker becomes a “man-in-the-middle”.
READ MORE…
Nowadays, security plays an important role in a company. Without any security solution implementation on our network, a user can simply “plug and play” into our network. The user may simple pick up a valid IP address or be assigned one automatically via DHCP. It is convenient, but not a good way if your network contains sensitive data. Worse, this user may have all the rights to your network so he can do dangerous things.
When your company grows bigger and bigger, there is a moment that you need to consider implementing security to your network. There are many ways to secure a network but AAA offers a complete solution. In this tutorial let’s find out about this security feature.
Before diving into AAA, let’s take an example of a user who wants to connect to our network.
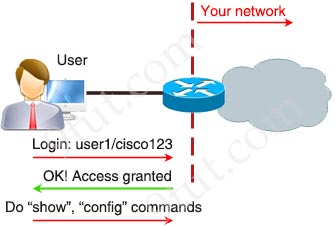
READ MORE…
In this tutorial we will learn in detail how Spanning Tree Protocol (STP) elect root port after choosing a root bridge.
Root port is the port that is closest to the root bridge, which means it is the port that receiving the lowest-cost BPDU from the root. Every non-root bridge must have a root port. All root ports are placed in forwarding state.
Spanning Tree Root Port election process (notice that it is Root Port election, not Root Bridge election process) in a Non-Root Switch includes the following steps:
1. Lowest accumulated cost on interfaces towards Root Bridge
2. Lowest Sender Bridge ID
3. Lowest Sender Port ID (= Port Priority + Port Number) (so port priority is compared first then to Port number)
Let’s see an example below:
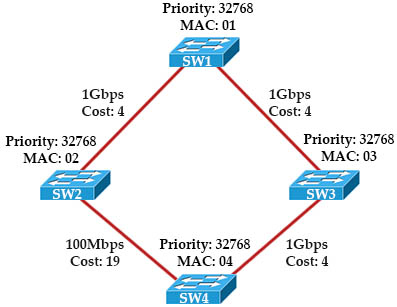
READ MORE…
The Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are the two most popular protocols in the transport layer. They ensures that messages are delivered error-free, in sequence, and with no losses or duplication. The key difference between TCP and UDP is that TCP provides a wide variety of services to applications, whereas UDP does not. At the result of this, TCP is much more complex than UDP so this tutorial is dedicated to explore TCP in detail but we still compare them.
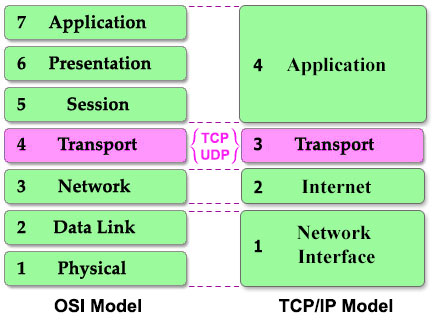
Both TCP and UDP are protocols at the Transport layer (of both OSI and TCP/IP model) but why we need both of them? The answer is:
+ TCP is slower but reliable
+ UDP is faster but unreliable
READ MORE…
Unlike LAN which is used effectively in relatively small geographic areas, WAN services help connect networks at a broad geographic distance, from a few to thousands of kilometers. Let’s see the network below, while LANs are used inside buildings like Home, Office, Internet Service Provider (ISP)… WANs are often used to connect between them. By the way, Internet is the largest WAN nowadays.
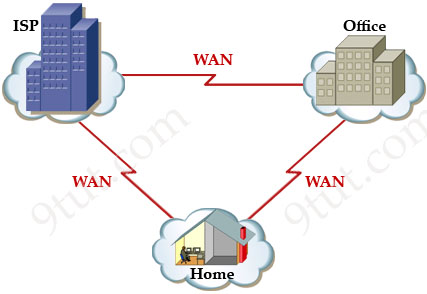
Because of long distance connection, individuals usually do not own WAN (unlike LAN which they often own it). They do not have the rights to bury a long cable between buildings either. Therefore they hire available network service providers, such as ISPs, cable or telephone companies… in their cities instead. This helps reduce the connection cost very much.
READ MORE…
In IP environment, before a computer can communicate to another one, they need to have their own IP addresses. There are two ways of configuring an IP address on a device:
+ Statically assign an IP address. This means we manually type an IP address for this computer
+ Use a protocol so that the computer can obtain its IP address automatically (dynamically). The most popular protocol nowadays to do this task is called Dynamic Host Configuration Protocol (DHCP) and we will learn about it in this tutorial.
A big advantage of using DHCP is the ability to join a network without knowing detail about it. For example you go to a coffee shop, with DHCP enabled on your computer, you can go online without doing anything. Next day you go online at your school and you don’t have to configure anything either even though the networks of the coffee shop and your school are different (for example, the network of the coffee shop is 192.168.1.0/24 while that of your company is 10.0.0.0/8). Really nice, right? Without DHCP, you have to ask someone who knows about the networks at your location then manually choosing an IP address in that range. In bad situation, your chosen IP can be same as someone else who is also using that network and an address conflict may occur. So how can DHCP obtain an suitable IP address for you automatically? Let’s find out.
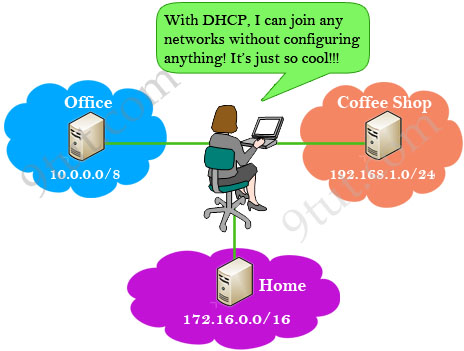
READ MORE…
Building a working network is important but monitoring its health is as important as building it. Luckily we have tools to make administrator’s life easier and SNMP is one among of them. SNMP presents in most of the network regardless of the size of that network. And understanding how SNMP works is really important and that what we will learn in this tutorial.
Understand SNMP
SNMP consists of 3 items:
+ SNMP Manager (sometimes called Network Management System – NMS): a software runs on the device of the network administrator (in most case, a computer) to monitor the network.
+ SNMP Agent: a software runs on network devices that we want to monitor (router, switch, server…)
+ Management Information Base (MIB): is the collection of managed objects. This components makes sure that the data exchange between the manager and the agent remains structured. In other words, MIB contains a set of questions that the SNMP Manager can ask the Agent (and the Agent can understand them). MIB is commonly shared between the Agent and Manager.
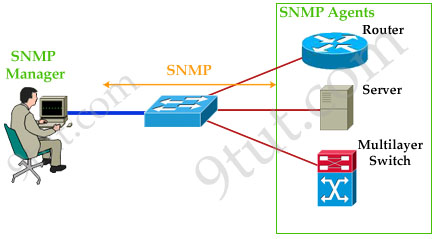
READ MORE…
As an administrator of a network, you have just completed all the configuration and they are working nicely. Now maybe the next thing you want to do is to set up something that can alert you when something goes wrong or down in your network. Syslog is an excellent tool for system monitoring and is almost always included in your distribution.
Places to store and display syslog messages
There are some places we can send syslog messages to:
| Place to store syslog messages |
Command to use |
| Internal buffer (inside a switch or router) |
logging buffered [size] |
| Syslog server |
logging |
| Flash memory |
logging file flash:filename |
| Nonconsole terminal (VTY connection…) |
terminal monitor |
| Console line |
logging console |
Note: If sent to a syslog server, messages are sent on UDP port 514.
By default, Cisco routers and switches send log messages to the console. We should use a syslog server to contain our logging messages with the logging command. Syslog server is the most popular place to store logging messages and administrators can easily monitor the wealth of their networks based on the received information.
READ MORE…
EtherChannel is the technology which is used to combine several physical links between switches or routers into one logical connection and treat them as a single link. Let’s take an example to see the benefits of this technology: Suppose your company has two switches connecting with each other via a FastEthernet link (100Mbps): 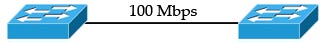 Your company is growing and you need to transfer more than 100 Mbps between these switches. If you only connect other links between the two switches it will not work because Spanning-tree protocol (STP) will block redundant links to prevent a loop:
Your company is growing and you need to transfer more than 100 Mbps between these switches. If you only connect other links between the two switches it will not work because Spanning-tree protocol (STP) will block redundant links to prevent a loop: 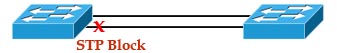 To extend the capacity of the link you have two ways:
To extend the capacity of the link you have two ways:
+ Buy two 1000Mbps (1Gbps) interfaces
+ Use EtherChannel technology to bundle them into a bigger link READ MORE…
In this tutorial we will learn what is HSRP and the need of HSRP in a network.
Most of the company in the world has a connection to the Internet. The picture below shows a most simple topology of such a company:
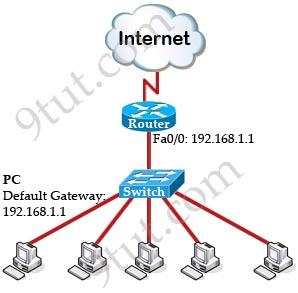
To make above topology work we need to:
+ Configure IP addresses on two interfaces of the Router. Suppose the IP address of Fa0/0 interface (the interface connecting to the switch) is 192.168.1.1.
+ Assign the IP addresses, default gateways and DNS servers on all PCs. In this case we have to set the default gateways to Fa0/0 interface (with the IP address 192.168.1.1) of the router. This can be done manually or automatically via DHCP.
READ MORE…
In the previous VLAN tutorial we learned how to use VLAN to segment the network and create “logical” broadcast domains. In this tutorial we will learn about InterVLAN Routing.
What is InterVLAN routing?
As we learned, devices within a VLAN can communicate with each other without the need of Layer 3 routing. But devices in separate VLANs require a Layer 3 routing device to communicate with one another. For example, in the topology below host A and B can communicate with each other without a router in the same VLAN 10; host C and D can communicate in the same VLAN 20. But host A can’t communicate with host C or D because they are in different VLANs.
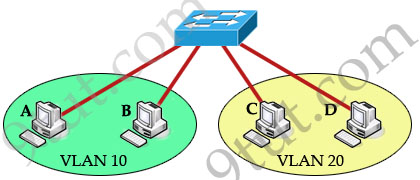
To allow hosts in different VLANs communicate with each other, we need a Layer 3 device (like a router) for routing:
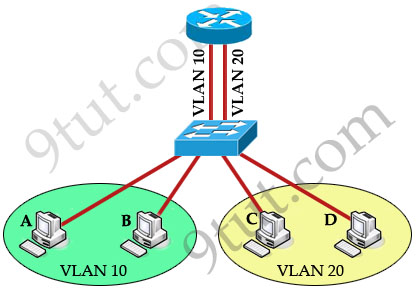
The routing traffic from one VLAN to another VLAN is called InterVLAN routing.
READ MORE…
In the previous tutorial we learned about the boot sequence of a Cisco router/switch. After that, the router will allow us to type commands but in different modes we can only used specific commands. So in this tutorial we will learn about the Command Line Interface (CLI) and different modes in a Cisco router/switch.
Below lists popular modes in Cisco switch/router:
| Router> |
User mode |
| Router# |
Privileged mode (Exec mode) |
| Router(config)# |
Configuration mode |
| Router(config-if)# |
Interface level (within configuration mode) |
| Router(config-router)# |
Routing engine level (within configuration mode) |
| Router(config-line)# |
Line level (vty, tty, async) within configuration mode |
Now let’s discuss each mode in more detail
READ MORE…
In this article we will learn about the main components of a Cisco router and how the boot process takes place.
Types of memory
Generally Cisco routers (and switches) contain four types of memory:
Read-Only Memory (ROM): ROM stores the router’s bootstrap startup program, operating system software, and power-on diagnostic test programs (POST).
Flash Memory: Generally referred to simply as “flash”, the IOS images are held here. Flash is erasable and reprogrammable ROM. Flash memory content is retained by the router on reload.
Random-Access Memory (RAM): Stores operational information such as routing tables and the running configuration file. RAM contents are lost when the router is powered down or reloaded.
Non-volatile RAM (NVRAM): NVRAM holds the router’s startup configuration file. NVRAM contents are not lost when the router is powered down or reloaded.
READ MORE…
Welcome to the most basic tutorial for networker! Understanding about OSI model is one of the most important tools to help you grasp how networking devices like router, switch, PC… work.
Let’s take an example in our real life to demonstrate the OSI model. Maybe you have ever sent a mail to your friend, right? To do it, you have to follow these steps:
1. Write your letter
2. Insert it into an envelope
3. Write information about sender and receiver on that envelope
4. Stamp it
5. Go to the post office and drop it into a mail inbox
From the example above, I want to imply we have to go through some steps in a specific order to complete a task. It is also applied for two PCs to communicate with each other. They have to use a predefined model, named OSI, to complete each step. There are 7 steps in this model as listed below:
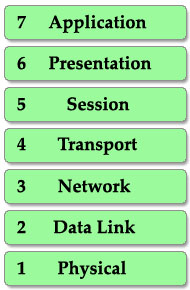
This is also the well-known table of the OSI model so you must take time to learn by heart. A popular way to remember this table is to create a fun sentence with the first letters of each layer. For example: All People Seem To Need Data Processing or a more funny sentence sorted from layer 1 to layer 7: Please Do Not Throw Sausage Pizza Away.
READ MORE…
In this article, we will learn how to subnet and make subnetting an easy task.
The table below summarizes the possible network numbers, the total number of each type, and the number of hosts in each Class A, B, and C network.
| |
Default subnet mask |
Range |
| Class A |
255.0.0.0 (/8) |
1.0.0.0 – 126.255.255.255 |
| Class B |
255.255.0.0 (/16) |
128.0.0.0 – 191.255.255.255 |
| Class C |
255.255.255.0 (/24) |
192.0.0.0 – 223.255.255.255 |
Table 1 – Default subnet mask & range of each class
Class A addresses begin with a 0 bit. Therefore, all addresses from 1.0.0.0 to 126.255.255.255 belong to class A (1=0000 0001; 126 = 0111 1110).
The 0.0.0.0 address is reserved for default routing and the 127.0.0.0 address is reserved for loopback testing so they don’t belong to any class.
Class B addresses begin with a 1 bit and a 0 bit. Therefore, all addresses from 128.0.0.0 to 191.255.255.255 belong to class B (128=1000 0000; 191 = 1011 1111).
Class C addresses begin with two 1 bits and a 0 bit. Class C addresses range from 192.0.0.0 to 223.255.255.255 (192 = 1100 0000; 223 = 1101 1111).
Class D & E are used for Multicast and Research purposes and we are not allowed to subnet them so they are not mentioned here.
Note: The number behind the slash notation (/) specifies how many bits are turned on (bit 1). For example:
+ “/8” equals “1111 1111.0000 0000.0000 0000.0000 0000” -> 8 bits are turned on (bit 1)
+ “/12” equals “1111 1111.1111 0000.0000 0000.0000 0000” -> 12 bits are turned on (bit 1)
+ “/28” equals “1111 1111.1111 1111.1111 1111.1111 0000” -> 28 bits are turned on (bit 1)
+ “/32” equals “1111 1111.1111 1111.1111 1111.1111 1111” -> 32 bits are turned on (bit 1) and this is also the maximum value because all bits are turned on.
The slash notation (following with a number) is equivalent to a subnet mask. If you know the slash notation you can figure out the subnet mask and vice versa. For example, “/8” is equivalent to “255.0.0.0”; “/12” is equivalent to “255.240.0.0”; “/28” is equivalent to “255.255.255.240”; “/32” is equivalent to “255.255.255.255”.
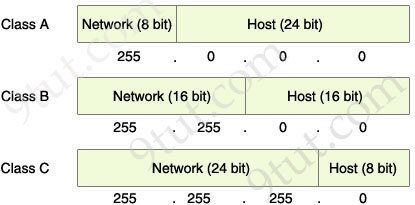
The Network & Host parts of each class by default
From the “default subnet mask” shown above, we can identify the network and host part of each class. Notice that in the subnet mask, bit 1 represents for Network part while bit 0 presents for Host part (255 equals to 1111 1111 and 0 equals to 0000 0000 in binary form).
READ MORE…
Note: Frame Relay is no longer a topic in CCNAv3 200-125 exam.
Let’s start this article with the question: Why do we need Frame Relay?
Let’s take a simple example. Suppose you are working in a big company and your company has just expanded to two new locations. The main site is connected to two branch offices, named Branch 1 & Branch 2 and your boss wants these two branches can communicate with the main site. The most simple solution is to connect them directly (called a leased line) as shown below:
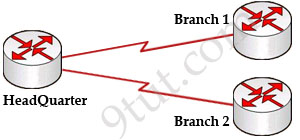
To connect to these two branches, the main site router, HeadQuarter, requires two serial interfaces which a router can provide. But what happens when the company expands to 10 branches, 50 branches? For each point-to-point line, HeadQuarter needs a separate physical serial interface (and maybe a separate CSU/DSU if it is not integrated into the WAN card). As you can imagine, it will need many routers with many interfaces and lots of rack space for the routers and CSU/DSUs. Maybe we should use another solution for this problem? Luckily, Frame Relay can do it!
READ MORE…
In this article we will discuss about Wireless technologies mentioned in CCNA.
Wireless LAN (WLAN) is very popular nowadays. Maybe you have ever used some wireless applications on your laptop or cellphone. Wireless LANs enable users to communicate without the need of cable. Below is an example of a simple WLAN:
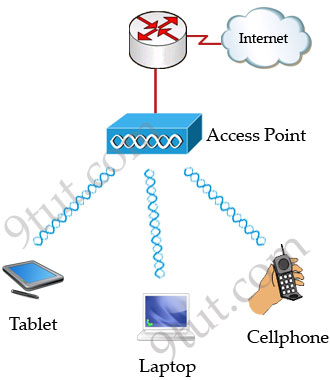
Each WLAN network needs a wireless Access Point (AP) to transmit and receive data from users. Unlike a wired network which operates at full-duplex (send and receive at the same time), a wireless network operates at half-duplex so sometimes an AP is referred as a Wireless Hub.
READ MORE…
VLAN Introduction
“A virtual LAN (VLAN) is a group of networking devices in the same broadcast domain”
It is the concept of VLAN that most of the books are using but it doesn’t help us understand the benefits of VLANs. If you ask “What is a LAN?” you will receive the same answer: it is also a group of networking devices in the same broadcast domain!
To make it clearer, I expanded the above statement into a bit longer statement :)
“A virtual LAN (VLAN) is a group of networking devices in the same broadcast domain, logically”
It means that the devices in the same VLAN may be widely separated in the network, both by geography and location. VLANs logically segment the network into different broadcast domains so that packets are only switched between ports that are designated for the same VLAN.
Let’s take an example to understand the benefits of VLAN. Suppose you are working in a big company with many departments, some of them are SALES and TECHNICAL departments. You are tasked to separate these departments so that each of them can only access specific resources in the company.
This task is really easy, you think. To complete this task, you just need to use different networks for these departments and use access-list to allow/deny that network to a specific resource. For example, you assign network 192.168.1.0/24 for SALES and 192.168.2.0/24 for TECH. At the “Company router” you apply an access-list to filter traffic from these networks. Below is the topology of your network without VLANs:
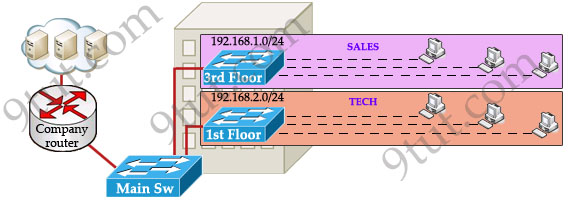
READ MORE…
This topic describes the features that VLAN Trunking Protocol (VTP) offers to support VLANs. To help you understand the basic concept, this is a summary of what VTP is:
“VTP allows a network manager to configure a switch so that it will propagate VLAN configurations to other switches in the network”
VTP minimizes misconfigurations and configuration inconsistencies that can cause problems, such as duplicate VLAN names or incorrect VLAN-type specifications. VTP helps you simplify management of the VLAN database across multiple switches.
VTP is a Cisco-proprietary protocol and is available on most of the Cisco switches.
Why we need VTP?
To answer this question, let’s discuss a real and popular network topology.
Suppose you are working in a medium company in a 5-floor office. You assigned each floor to a switch for easy management and of course they can be assigned to different VLANs. For example, your bosses can sit in any floor and still access Manage VLAN (VLAN 7). Your technical colleagues can sit anywhere on the floors to access Technical VLAN (VLAN 4). This is the best design because each person’s permission is not limited by the physical location.
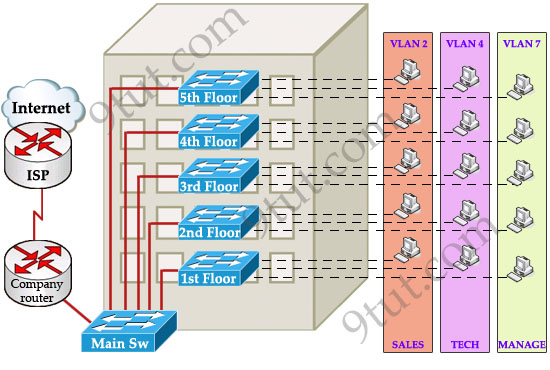
READ MORE…
Internet has been growing extremely fast so the IPv4 addresses are quickly approaching complete depletion. Although many organizations already use Network Address Translators (NATs) to map multiple private address spaces to a single public IP address but they have to face with other problems from NAT (the use of the same private address, security…). Moreover, many other devices than PC & laptop are requiring an IP address to go to the Internet. To solve these problems in long-term, a new version of the IP protocol – version 6 (IPv6) was created and developed.
IPv6 was created by the Internet Engineering Task Force (IETF), a standards body, as a replacement to IPv4 in 1998. So what happened with IPv5? IP Version 5 was defined for experimental reasons and never was deployed.
While IPv4 uses 32 bits to address the IP (provides approximately 232 = 4,294,967,296 unique addresses – but in fact about 3.7 billion addresses are assignable because the IPv4 addressing system separates the addresses into classes and reserves addresses for multicasting, testing, and other specific uses), IPv6 uses up to 128 bits which provides 2128 addresses or approximately 3.4 * 1038 addresses. Well, maybe we should say it is extremely extremely extremely huge :)
READ MORE…
Note: Before reading this article you should understand how STP works. So if you are not sure about STP, please read my article about Spanning Tree Protocol tutorial first.
Rapid Spanning Tree Protocol (RSTP)
One big disadvantage of STP is the low convergence which is very important in switched network. To overcome this problem, in 2001, the IEEE with document 802.1w introduced an evolution of the Spanning Tree Protocol: Rapid Spanning Tree Protocol (RSTP), which significantly reduces the convergence time after a topology change occurs in the network. While STP can take 30 to 50 seconds to transit from a blocking state to a forwarding state, RSTP is typically able to respond less than 10 seconds of a physical link failure.
RSTP works by adding an alternative port and a backup port compared to STP. These ports are allowed to immediately enter the forwarding state rather than passively wait for the network to converge.
RSTP bridge port roles:
* Root port – A forwarding port that is the closest to the root bridge in terms of path cost
* Designated port – A forwarding port for every LAN segment
* Alternate port – A best alternate path to the root bridge. This path is different than using the root port. The alternative port moves to the forwarding state if there is a failure on the designated port for the segment.
* Backup port – A backup/redundant path to a segment where another bridge port already connects. The backup port applies only when a single switch has two links to the same segment (collision domain). To have two links to the same collision domain, the switch must be attached to a hub.
* Disabled port – Not strictly part of STP, a network administrator can manually disable a port
Now let’s see an example of three switches below:
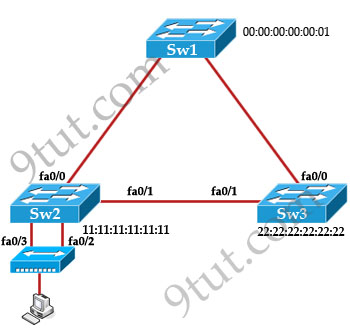
READ MORE…
To provide for fault tolerance, many networks implement redundant paths between devices using multiple switches. However, providing redundant paths between segments causes packets to be passed between the redundant paths endlessly. This condition is known as a bridging loop.
(Note: the terms bridge, switch are used interchangeably when discussing STP)
To prevent bridging loops, the IEEE 802.1d committee defined a standard called the spanning tree algorithm (STA), or spanning tree protocol (STP). Spanning-Tree Protocol is a link management protocol that provides path redundancy while preventing undesirable loops in the network. For an Ethernet network to function properly, only one active path can exist between two stations.
Let’s see a situation when there is no loop-avoidance process in operation. Suppose you have two switches connected with redundant links. One switch connected to PC A and the other switch connected to PC B.
Now PC A wants to talk to PC B. It then sends a broadcast, say an Address Resolution Protocol (ARP) to find out where the location of PC B, the green arrow shows a broadcast frame sent by PC A.
When the switch A receives a broadcast frame, it forwards that frame to all ports except the port where it receives the request -> SwA forwards that ARP frame out of fa0/0 and fa0/1 ports.

READ MORE…
To go to the Internet we need to get an public IP address and it is unique all over the world. If each host in the world required a unique public IP address, we would have run out of IP address years ago. But by using Network Address Translation (NAT) we can save tons of IP addresses for later uses. We can understand NAT like this:
“NAT allows a host that does not have a valid registered IP address to communicate with other hosts through the Internet”
For example your computer is assigned a private IP address of 10.0.0.9 and of course this address can not be routed on the internet but you can still access the internet. This is because your router (or modem) translates this address into a public IP address, 123.12.23.1 for example, before routing your data into the internet.
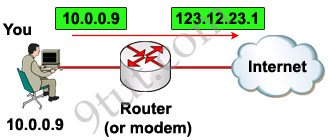
READ MORE…
In this tutorial we will learn about access list.
Access control lists (ACLs) provide a means to filter packets by allowing a user to permit or deny IP packets from crossing specified interfaces. Just imagine you come to a fair and see the guardian checking tickets. He only allows people with suitable tickets to enter. Well, an access list’s function is same as that guardian.
Access lists filter network traffic by controlling whether packets are forwarded or blocked at the router’s interfaces based on the criteria you specified within the access list.
To use ACLs, the system administrator must first configure ACLs and then apply them to specific interfaces. There are 3 popular types of ACL: Standard, Extended and Named ACLs.
READ MORE…
In this tutorial we will learn about RIP routing protocol
Routing Information Protocol (RIP) is a distance-vector routing protocol which is based on Bellman-Ford algorithm. Routers using Distance Vector routing protocols do not posses the topological information about the network but instead rely on the neighbors information (so this method is known as routing by rumor). RIP sends the complete routing table out to all active interfaces every 30 seconds. RIP only uses hop count (the number of routers) to determine the best way to a remote network.
Note: RIP v1 is a classful routing protocol but RIP v2 is a classless routing protocol.
Classful routing protocols do not include the subnet mask with the network address in routing updates, which can cause problems with discontiguous subnets or networks that use Variable-Length Subnet Masking (VLSM). Fortunately, RIPv2 is a classless routing protocol so subnet masks are included in the routing updates, making RIPv2 more compatible with modern routing environments.
Distance vector protocols advertise routing information by sending messages, called routing updates, out the interfaces on a router.
READ MORE…
In this article we will mention about the EIGRP protocol.
In the past, Enhanced Interior Gateway Routing Protocol (EIGRP) is a Cisco-proprietary routing protocol but from March-2013 Cisco opens up EIGRP as an open standard in order to help companies operate in a multi-vendor environment. EIGRP is a classless routing protocol, meaning that it sends the subnet mask of its interfaces in routing updates, which use a complex metric based on bandwidth and delay.
EIGRP is referred to as a hybrid routing protocol because it has the characteristics of both distance-vector and link-state protocols but now Cisco refers it as an advanced distance vector protocol.
Notice: the term “hybrid” is misleading because EIGRP is not a hybrid between distance vector and link-state routing protocols. It is a distance vector routing protocol with enhanced features.
EIGRP is a powerful routing protocol and it is really standout from its ancestor IGRP. The main features are listed below:
+ Support VLSM and discontiguous networks
+ Use Reliable Transport Protocol (RTP) to delivery and reception of EIGRP packets
+ Use the best path selection Diffusing Update Algorithm (DUAL), guaranteeing loop-free paths and backup paths throughout the routing domain
+ Discover neighboring devices using periodic Hello messages to discover and monitor connection status with its neighbors
+ Exchange the full routing table at startup and send partial* triggered updates thereafter (not full updates like distance-vector protocols) and the triggered updates are only sent to routers that need the information. This behavior is different from the link-state protocol in which an update will be sent to all the link-state routers within that area. For example, EIGRP will send updates when a new link comes up or a link becoming unavailable
+ Supports multiple protocols: EIGRP can exchange routes for IPv4, IPv6, AppleTalk and IPX/SPX networks
+ Load balancing: EIGRP supports unequal metric load balancing, which allows administrators to better distribute traffic flow in their networks.
* Notice: The term “partial” means that the update only includes information about the route changes.
READ MORE…
In this article we will learn about the OSPF Routing Protocol
Open-Shortest-Path-First (OSPF) is the most widely used interior gateway protocol routing protocol on the world because it is a public (non-proprietary) routing protocol while its biggest rival, EIGRP, is a Cisco proprietary protocol so other vendors can’t use it (edit: EIGRP has become a public routing protocol since 2013). OSPF is a complex link-state routing protocol. Link-state routing protocols generate routing updates only when a change occurs in the network topology. When a link changes state, the device that detected the change creates a link-state advertisement (LSA) concerning that link and sends to all neighboring devices using a special multicast address. Each routing device takes a copy of the LSA, updates its link-state database (LSDB), and forwards the LSA to all neighboring devices.
Note:
+ OSPF routers use LSA (Link State Advertisement)to describe its link state. LSDB stores all LSAs.
+ A router uses Router LSA to describe its interface IP addresses.
+ After OSPF is started on a router, it creates LSDB that contains one entry: this router’s Router LSA.
There are five types of OSPF Link-State Packets (LSPs).
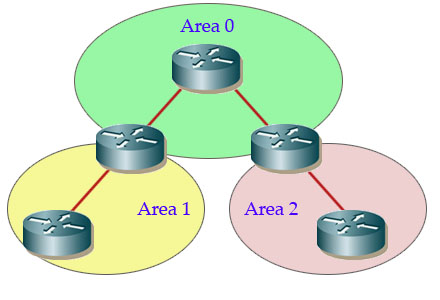
READ MORE…























 To extend the capacity of the link you have two ways:
To extend the capacity of the link you have two ways: 













