SDN Solution
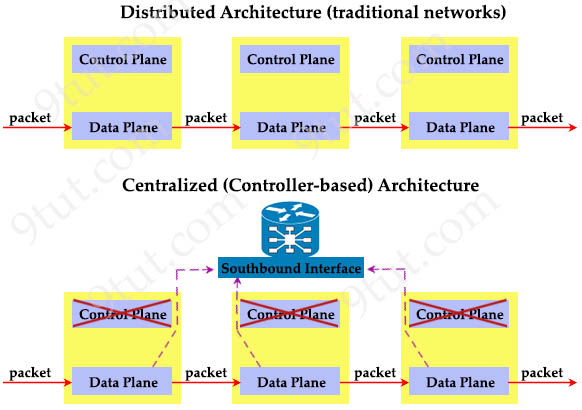
| SDN Quick Summary Everything that networking devices do can be categorized into three planes: Data Plane, Control Plane and Management Plane. + Data Plane: responsible for the switching of packets through the router. In short, it includes any action after receiving data (processing, encapsulating/decapsulating, matching destination MAC & IP addresses, forwarding, QoS, filtering with access-list) + Control Plane: responsible for maintaining sessions and exchanging protocol information with other network devices. It consists of dynamic IP routing protocols (OSPF, EIGRP, BGP…), the RIB, routing updates, in addition to other protocols such as STP, ARP, ICMP, PIM, IGMP, LACP… + Management Plane: is used to manage a device through its connection to the network. Examples of protocols processed in the management plane include Simple Network Management Protocol (SNMP), Telnet, File Transfer Protocol (FTP), Secure FTP, and Secure Shell (SSH). These management protocols are used for monitoring and for command-line interface (CLI) access Most traditional devices use a distributed architecture, in which each control plane is resided in a networking device. Therefore they need to communicate with each other via messages to work correctly. In constrast to distributed architecture, centralized (or controller-based) architectures centralizes the control of networking devices into one device, called SDN controller.
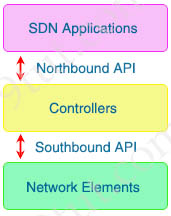
Now, in turn, the networking administrators and SDN applications want to control the controller! So the controller need a northbound interface (NBI) to communicate with us. The NBI applications included various network services, including network virtualization, dynamic virtual network provisioning, firewall monitoring, user identity management and access policy control.
– REST (Representational State Transfer) describes a type of API that allows applications to sit on different hosts, using HTTP messages to transfer data over the API. |
Question 1
Explanation
Cisco Application Policy Infrastructure Controller (APIC)
The infrastructure controller is the main architectural component of the Cisco ACI solution. It is the unified point of automation and management for the Cisco ACI fabric, policy enforcement, and health monitoring. The APIC appliance is a centralized, clustered controller that optimizes performance and unifies operation of physical and virtual environments. The controller manages and operates a scalable multitenant Cisco ACI fabric.
Question 2
Explanation
A northbound interface is an interface that allows a particular component of a network to communicate with a higher-level component. Conversely, a southbound interface allows a particular network component to communicate with a lower-level component.
The northbound APIs on an SDN controller enable applications and orchestration systems to program the network and request services from it.
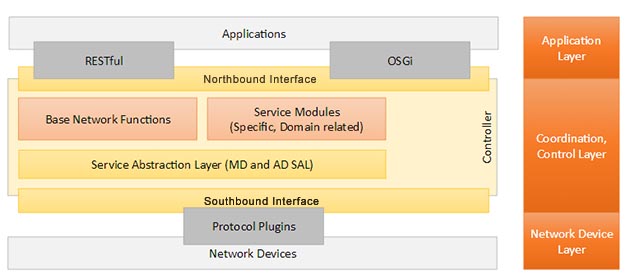
Southbound interfaces are implemented with a Service Abstraction Layer (SAL) which speak to network devices using SNMP and CLI (Command Line Interface) of the elements that make up the network. The main functions of SAL are:
+ Expose device services and capabilities to apps
+ Determine how to fulfill requested service irrespective of the underlying protocol
Note:
+ An API is a method for one application (program) to exchange data with another application.
+ Interface here refers to the “software interface”, not the physical interfaces.
Question 3
Explanation
The APIC-EM platform delivers many significant benefits. For example, it:
+ Creates an intelligent, open, programmable network with open APIs
+ Can help customers save time, resources, and costs through advanced automation services
+ Can transform business-intent policies into dynamic network configuration
+ Provides a single point for network-wide automation and control
Question 4
Explanation
Cisco APIC-EM supports the following policy analysis features:
+ Inspection, interrogation, and analysis of network access control policies.
+ Ability to trace application specific paths between end devices to quickly identify ACLs in use and problem areas.
+ Enables ACL change management with easy identification of conflicts and shadows -> Maybe B is the most suitable answer.
The ACL trace tool can only help us to identify which ACL on which router is blocking or allowing traffic. It cannot help identify redundant/shadow rules.
Note:
Cisco Application Policy Infrastructure Controller Enterprise Module (APIC-EM) is a Cisco Software Defined Networking (SDN) controller, which uses open APIs for policy-based management and security through a single controller, abstracting the network and making network services simpler. APIC-EM provides centralized automation of policy-based application profiles.
Reference: CCNA Routing and Switching Complete Study Guide
Cisco Intelligent WAN (IWAN) application simplifies the provisioning of IWAN network profiles with simple business policies. The IWAN application defines business-level preferences by application or groups of applications in terms of the preferred path for hybrid WAN links. Doing so improves the application experience over any connection and saves telecom costs by leveraging cheaper WAN links.
Shadow rules are the rules that are never matched (usually because of the first rules). For example two access-list statements:
access-list 100 permit ip any any
access-list 100 deny tcp host A host B
Then the second access-list statement would never be matched because all traffic have been already allowed by the first statement. In this case we call statement 1 shadows statement 2.
Question 5
Explanation
The ACL Path Analysis tool in APIC-EM can help to identify where the traffic was blocked in the transmission.
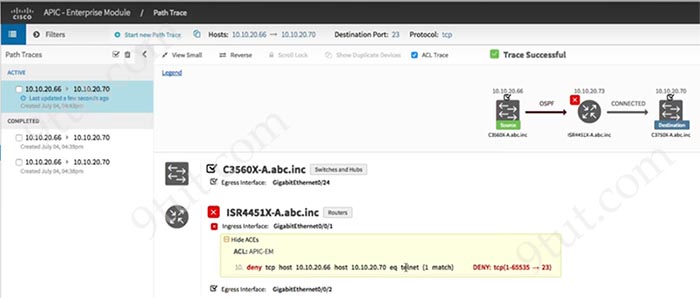
Question 6
Explanation
Icon ![]() means “there are ACLs that permit the traffic applied on the interface”.
means “there are ACLs that permit the traffic applied on the interface”.
Icon ![]() means “traffic may or may not be blocked. For example, if your traffic matches a deny access control entry (ACE), traffic is denied. However, if your traffic matches any other ACEs, it is permitted. You can get this type of results if you leave out the protocol, source port, or destination port when defining a path trace”.
means “traffic may or may not be blocked. For example, if your traffic matches a deny access control entry (ACE), traffic is denied. However, if your traffic matches any other ACEs, it is permitted. You can get this type of results if you leave out the protocol, source port, or destination port when defining a path trace”.
Icon ![]() means “there is an ACL on the device or interface that is blocking the traffic on the path”.
means “there is an ACL on the device or interface that is blocking the traffic on the path”.
Icon ![]() means “there are no ACLs applied on the interface”.
means “there are no ACLs applied on the interface”.